Search the Community
Showing results for tags 'Certificate'.
-
Curious if anyone knows if the permissions UDF can be used with certificates and if so, how. This is the code in the UDF for $_SE_OBJECT_TYPE which doesn't state anything about certs and not sure if it would fall under one of the object types listed: Global Enum _ ;$_SE_OBJECT_TYPE $SE_UNKNOWN_OBJECT_TYPE = 0, _ ;Unknown object type. $SE_FILE_OBJECT, _ ;Indicates a file or directory. Can be an absolute path, such as FileName.dat, C:\DirectoryName\FileName.dat, or a handle to an opened file $SE_SERVICE, _;Indicates a Windows service. A service object can be a local service, such as ServiceName, or a remote service, such as \\ComputerName\ServiceName, or a handle to a service $SE_PRINTER, _;Indicates a printer. A printer object can be a local printer, such as PrinterName, or a remote printer, such as \\ComputerName\PrinterName. $SE_REGISTRY_KEY, _;Indicates a registry key. The names can be in the format 'HKLM\SOFTWARE\Example', or 'HKEY_LOCAL_MACHINE\SOFTWARE\Example'. It can also be a handle to a registry key $SE_LMSHARE, _;Indicates a network share. A share object can be local, such as ShareName, or remote, such as \\ComputerName\ShareName. $SE_KERNEL_OBJECT, _;Indicates a local kernel object. All types of kernel objects are supported. ie, A process handle obtained with _Permissions_OpenProcess $SE_WINDOW_OBJECT, _;Indicates a window station or desktop object on the local computer. $SE_DS_OBJECT, _;Indicates a directory service object or a property set or property of a directory service object. e.g.CN=SomeObject,OU=ou2,OU=ou1,DC=DomainName,DC=CompanyName,DC=com,O=internet $SE_DS_OBJECT_ALL, _;Indicates a directory service object and all of its property sets and properties. $SE_PROVIDER_DEFINED_OBJECT, _;Indicates a provider-defined object. $SE_WMIGUID_OBJECT, _;Indicates a WMI object. $SE_REGISTRY_WOW64_32KEY;Indicates an object for a registry entry under WOW64. ;$_SE_OBJECT_TYPE What I'm trying to do is add another user to a cert in Certificates (Local Computer) > Personal > Certificates as if using the "manage private keys" command via the MMC. Thanks...
-
Greetings, I want use WinHttpRequest to access a OpenShift API server, it use a self signed certificate. Does now work... I never try with a self signed certificate, how do this? Best regards Global $oHTTP = ObjCreate("winhttp.winhttprequest.5.1") $oHTTP.Open("GET", "https://openshift.domain:1234/api/", False) $oHttp.Option(4) = 0x0100 + 0x0200 + 0x1000 + 0x2000 $oHTTP.Option(9) = 0x0080 ;WinHttpRequestOption_SecureProtocols ;~ $oHttp.SetClientCertificate("LOCAL_MACHINE\\Personal\\certificado.crt") $oHttp.Send() $oHttp.WaitForResponse() Local $oAllHeaders = $oHttp.GetAllResponseHeaders() $oReceived = $oHttp.ResponseText $oStatusCode = $oHttp.Status $oHttp = 0 If $oStatusCode = 200 Then ConsoleWrite("$oAllHeaders--------------------" & @LF & $oAllHeaders & "$oAllHeaders--------------------" & @LF) Else ConsoleWrite("< error = " & $oReceived & @LF & $oAllHeaders & @LF) EndIf
- 1 reply
-
- winhttprequest
- certificate
-
(and 2 more)
Tagged with:
-
Hi guys, I have a pretty advanced question... This is the issue i'm facing : On a regular basis we need to install pfx certificates (with password protection) on devices from external companies. To install the certificate we always have to contact the user, setup a really dull and long process to get an RDP session to that device, install the certificate. I'm looking for : a way to generate exe files on the fly, that will include the pfx file and password, and automatically install them without any interaction from the user, and the user not being able to retrieve the password to install the certificate. Question : Is this possible with AutoIT? And if so, does anyone have a working example for the certificate installation part or the auto generate with file include? Thx in advance colombeen
- 36 replies
-
- certificate
- pfx
-
(and 1 more)
Tagged with:
-
I can check this though signtool.exe and it results in the text output though below command. signtool.exe verify /v /pa "C:\test\ftdiport.cat"And this result the output in verbose mode in command prompt or we can redirect it to a text file as below. Verifying: C:\test\ftdiport.cat Signing Certificate Chain: Issued to: Class 3 Public Primary Certification Authority Issued by: Class 3 Public Primary Certification Authority Expires: 8/2/2028 5:29:59 AM SHA1 hash: 742C3192E607E424EB4549542BE1BBC53E6174E2 Issued to: VeriSign Class 3 Code Signing 2004 CA Issued by: Class 3 Public Primary Certification Authority Expires: 7/16/2014 5:29:59 AM SHA1 hash: 197A4AEBDB25F0170079BB8C73CB2D655E0018A4 Issued to: Future Technology Devices International Ltd Issued by: VeriSign Class 3 Code Signing 2004 CA Expires: 9/30/2010 5:29:59 AM SHA1 hash: 029E8FF6146EE9AEDA68092AB030057165B73A20 The signature is timestamped: 3/31/2010 6:10:55 PM Timestamp Verified by: Issued to: Thawte Timestamping CA Issued by: Thawte Timestamping CA Expires: 1/1/2021 5:29:59 AM SHA1 hash: BE36A4562FB2EE05DBB3D32323ADF445084ED656 Issued to: VeriSign Time Stamping Services CA Issued by: Thawte Timestamping CA Expires: 12/4/2013 5:29:59 AM SHA1 hash: F46AC0C6EFBB8C6A14F55F09E2D37DF4C0DE012D Issued to: VeriSign Time Stamping Services Signer - G2 Issued by: VeriSign Time Stamping Services CA Expires: 6/15/2012 5:29:59 AM SHA1 hash: ADA8AAA643FF7DC38DD40FA4C97AD559FF4846DE Successfully verified: C:\Users\ur00361883\Desktop\ftdiport.cat Number of files successfully Verified: 1 Number of warnings: 0 Number of errors: 0 One option is to parse this file and I need to get below details. Catalog file is Signed/Unsigned and Certificate issued for it and its expiry date. Is there any option like some libraries instead of parsing this text file whether in c#,vbscript,autoit or powershell or any platform. If no option, please guide me on how to parse this output.
-
Is there any library or api in Autoit to check whether a particular driver is signed or not and check for the certificate validity of the driver/catalog file if it is signed.?
- 3 replies
-
- certificate
- driver
-
(and 1 more)
Tagged with:
-
I'm trying to build a script to call some functions of a web service. I have found this example for doing SOAP ?do=embed' frameborder='0' data-embedContent> so I assume I can manually read out the wsdl file and figure out how to hand build a payload to do what I want ( I think, honestly this is all new to me). the problem I have is that the service requires authentication via client certificate. and I can't seem to find any example of how to use a webservice like that with autoit. I *might* have a basic auth option to access the service too but that's not 100% and even if I can I don't know how to do basic auth in autoit either. is this possible with autoit it (with either auth)? can anyone point me to some code?
- 1 reply
-
- web service
- authentication
-
(and 3 more)
Tagged with:
-

"EV" Code Signing Certificate
MrPinkComputerShrink posted a topic in AutoIt General Help and Support
Has anyone successfully applied an EV Code Signing Certificate to their .exe file created with AutoIt? If so, were there any additional steps required or was it just like the regular code signing Certificate? Reference: https://www.digicert.com/code-signing/ev-code-signing-compared.htm Thanks, Scott C.- 4 replies
-
- EV
- Certificate
-
(and 4 more)
Tagged with:
-
PE File Overlay Extraction (and Certificate info) Executable and other PE files can contain "overlays", which is data that is appended to the end of the file. This data can be important, such as setup packages, Authenticode signatures*, and overlays for AutoIt scripts. Or it could just be extra unneeded cruft (sometimes). Whatever the case is, I wanted to find a way to detect if this data was present. This project is actually a result of dealing with so-called 'File Optimizer' programs that would strip Overlay information from Executables (leaving compiled AutoIt scripts crippled!). And also a legit >answer to my topic in Help and Support. While future versions of AutoIt (new beta releases and any official release after v3.3.8.1) are putting tokenized scripts into a resource within the executable, all current compiled scripts are still put together with the tokenized script appended as an overlay. The UDF here allows you to detect any overlay a PE (Portable Executable) file may have, and allows you to extract the Overlay into a separate file - or alternatively extract the exe without the overlay. You can actually extract AutoIt scripts and write them to .A3X files using this method, if you so desire. But don't be a hacker! Mommy will scold you.. If you separate both the exe and overlay, you can combine them again using a simple file-append, something like: copy /b stripped.exe+script.a3x myscript.exe _ Anyway, the method to detect overlays is relatively simple - we need to look through the PE file's various headers and find out where the last section of data/code is and its size. If that last section doesn't reach the end of the file, then you will find an Overlay waiting at the end of the final section. However, there's an issue with Certificate Tables (or signatures) which makes it a bit more tricky to detect - basically the end of the last section and the beginning of the Certificate must be examined to find the sandwiched-in overlay. *Auhenticode signatures note: These and other certificates are actually linked to in the PE Data Directory, which I had missed in earlier versions. Now they are accounted for however, and not considered overlays nor are they allowed to be extracted (well, you could extract them but the signature is bound to the unique checksum of the file and needs to be referenced from the Data Directory). IMPORTANT: The example now queries which part to save, and "No" button means 'yes' to Exe extract. (I didn't want to mess around with creating dialog windows, sorry). So, here's the UDF with a working example (note the 128MB limit can easily be worked around): ; ======================================================================================================== ; <FilePEOverlayExtract.au3> ; ; UDF and Example of getting Overlay info and optionally extracting that info to a file. ; ; NOTE that this isn't intended to be used to hack or decompile AutoIt executables!! ; It's main purpose is to find Overlays and Certificates and extract/save or just report the info ; ; Functions: ; _PEFileGetOverlayInfo() ; Returns a file offset for overlay data (if found), and the size ; ; Author: Ascend4nt ; ======================================================================================================== ; Arry indexing Global Enum $PEI_OVL_START = 0, $PEI_OVL_SIZE, $PEI_CERT_START, $PEI_CERT_SIZE, $PEI_FILE_SIZE ; ---------------------- MAIN CODE ------------------------------- Local $sFile, $sLastDir, $sLastFile, $aOverlayInfo $sLastDir = @ScriptDir While 1 $sFile=FileOpenDialog("Select PE File To Find Overlay Data In",$sLastDir,"PE Files (*.exe;*.dll;*.drv;*.scr;*.cpl;*.sys;*.ocx;*.tlb;*.olb)|All Files (*.*)",3,$sLastFile) If @error Or $sFile="" Then Exit $sLastFile=StringMid($sFile,StringInStr($sFile,'\',1,-1)+1) $sLastDir=StringLeft($sFile,StringInStr($sFile,'\',1,-1)-1) $aOverlayInfo = _PEFileGetOverlayInfo($sFile) If $aOverlayInfo[$PEI_OVL_START] = 0 Then ConsoleWrite("Failed Return from _PEGetOverlayOffset(), @error = " & @error & ", @extended = " & @extended & @CRLF) MsgBox(64, "No Overlay Found", "No overlay found in " & $sLastFile) ContinueLoop EndIf ConsoleWrite("Return from _PEFileGetOverlayInfo() = " & $aOverlayInfo[$PEI_OVL_START] & ", @extended = " & $aOverlayInfo[$PEI_OVL_SIZE] & @CRLF) If $aOverlayInfo[$PEI_OVL_START] Then Local $hFileIn = -1, $hFileOut = -1, $sOutFile, $iMsgBox, $bBuffer, $bSuccess = 0 $iMsgBox = MsgBox(35, "Overlay found in " & $sLastFile, "Overlay Found. File size: " & $aOverlayInfo[$PEI_FILE_SIZE] & ", Overlay size: " & $aOverlayInfo[$PEI_OVL_SIZE] & @CRLF & @CRLF & _ "Would you like to:" & @CRLF & _ "[Yes]: extract and save Overlay" & @CRLF & _ "[No]: extract Exe without Overlay" & @CRLF & _ "[Cancel]: Do Nothing") If $iMsgBox = 6 Then If $aOverlayInfo[$PEI_OVL_SIZE] > 134217728 Then MsgBox(48, "Overlay is too huge", "Overlay is > 128MB, skipping..") ContinueLoop EndIf $sOutFile = FileSaveDialog("Overlay - SAVE: Choose a file to write Overlay data to (from " & $sLastFile&")", $sLastDir, "All (*.*)", 2 + 16) If Not @error Then While 1 $hFileOut = FileOpen($sOutFile, 16 + 2) If $hFileOut = -1 Then ExitLoop $hFileIn = FileOpen($sFile, 16) If $hFileIn = -1 Then ExitLoop If Not FileSetPos($hFileIn, $aOverlayInfo[$PEI_OVL_START], 0) Then ExitLoop ; AutoIt 2/3 Signature check requires 32 bytes min. If $aOverlayInfo[$PEI_FILE_SIZE] > 32 Then $bBuffer = FileRead($hFileIn, 32) If @error Then ExitLoop ; AutoIt2 & AutoIt3 signatures If BinaryMid($bBuffer, 1, 16) = "0xA3484BBE986C4AA9994C530A86D6487D" Or _ BinaryMid($bBuffer, 1 + 16, 4) = "0x41553321" Then ; "AU3!" ConsoleWrite("AutoIt overlay file found" & @CRLF) EndIf FileWrite($hFileOut, $bBuffer) ; subtract amount we read in above $bSuccess = FileWrite($hFileOut, FileRead($hFileIn, $aOverlayInfo[$PEI_OVL_SIZE] - 32)) Else $bSuccess = FileWrite($hFileOut, FileRead($hFileIn, $aOverlayInfo[$PEI_OVL_SIZE])) EndIf ExitLoop WEnd If $hFileOut <> -1 Then FileClose($hFileOut) If $hFileIn <> -1 Then FileClose($hFileIn) EndIf ElseIf $iMsgBox = 7 Then If $aOverlayInfo[$PEI_FILE_SIZE] - $aOverlayInfo[$PEI_OVL_SIZE] > 134217728 Then MsgBox(48, "EXE is too huge", "EXE (minus overlay) is > 128MB, skipping..") ContinueLoop EndIf $sOutFile = FileSaveDialog("EXE {STRIPPED} - SAVE: Choose a file to write EXE (minus Overlay) to. (from " & $sLastFile&")", $sLastDir, "All (*.*)", 2 + 16) If Not @error Then $bSuccess = FileWrite($sOutFile, FileRead($sFile, $aOverlayInfo[$PEI_OVL_START])) EndIf Else ContinueLoop EndIf If $bSuccess Then ShellExecute(StringLeft($sOutFile,StringInStr($sOutFile,'\',1,-1)-1)) Else MsgBox(64, "Error Opening or writing to file", "Error opening, reading or writing overlay info") EndIf EndIf WEnd Exit ; ------------------------ UDF Function ---------------------------- ; =================================================================================================================== ; Func _PEFileGetOverlayInfo($sPEFile) ; ; Returns information on Overlays present in a Windows PE file (.EXE, .DLL etc files), as well as Certificate Info. ; ; Only certain executables contain Overlays, and these are always located after the last PE Section, ; and most times before any Certificate info. Setup/install programs typically package their data in Overlays, ; and AutoIt compiled executables (at least up to v3.3.8.1) contain an overlay in .A3X tokenized format. ; ; Certificate info is available with or without an overlay, and comes after the last section and typically after ; an Overlay. Certificates are included with signed executables (such as Authenticode-signed) ; ; The returned info can be used to examine or extract the Overlay or Certificate, or just to examine the data ; (for example, to see if its an AutoIt tokenized script). ; ; NOTE: Any Overlays packaged into Certificate blocks are ignored, and the methods to extract this info may ; fail if the Certificate Table entries have their sizes modified to include the embedded Overlay. ; ; The returned information can be useful in preventing executable 'optimizers' from stripping the Overlay info, ; which was the primary intent in creating this UDF. ; ; ; Returns: ; Success: A 5-element array, @error = 0 ; [0] = Overlay Start (if any) ; [1] = Overlay Size ; [2] = Certificate Start (if any) ; [3] = Certificate Size ; [4] = File Size ; ; Failure: Same 5-element array as above (with all 0's), and @error set: ; @error = -1 = Could not open file ; @error = -2 = FileRead error (most likely an invalid PE file). @extended = FileRead() @error ; @error = -3 = FileSetPos error (most likely an invalid PE file) ; @error = 1 = File does not exist ; @error = 2 = 'MZ' signature could not be found (not a PE file) ; @error = 3 = 'PE' signature could not be found (not a PE file) ; @error = 4 = 'Magic' number not recognized (not PE32, PE32+, could be 'ROM (0x107), or unk.) @extended=number ; ; Author: Ascend4nt ; =================================================================================================================== Func _PEFileGetOverlayInfo($sPEFile) ;~ If Not FileExists($sPEFile) Then Return SetError(1,0,0) Local $hFile, $nFileSize, $bBuffer, $iOffset, $iErr, $iExit, $aRet[5] = [0, 0, 0, 0] Local $nTemp, $nSections, $nDataDirectories, $nLastSectionOffset, $nLastSectionSz Local $iSucces=0, $iCertificateAddress = 0, $nCertificateSz = 0, $stEndian = DllStructCreate("int") $nFileSize = FileGetSize($sPEFile) $hFile = FileOpen($sPEFile, 16) If $hFile = -1 Then Return SetError(-1,0,$aRet) ; A once-only loop helps where "goto's" would be helpful Do ; We keep different exit codes for different operations in case of failure (easier to track down what failed) ; The function can be altered to remove these assignments of course $iExit = -2 $bBuffer = FileRead($hFile, 2) If @error Then ExitLoop $iExit = 2 ;~ 'MZ' in hex (endian-swapped): If $bBuffer <> 0x5A4D Then ExitLoop ;ConsoleWrite("MZ Signature found:"&BinaryToString($bBuffer)&@CRLF) $iExit = -3 ;~ Move to Windows PE Signature Offset location If Not FileSetPos($hFile, 0x3C, 0) Then ExitLoop $iExit = -2 $bBuffer = FileRead($hFile, 4) If @error Then ExitLoop $iOffset = Number($bBuffer) ; Though the data is in little-endian, because its a binary variant, the conversion works ;ConsoleWrite("Offset to Windows PE Header="&$iOffset&@CRLF) $iExit = -3 ;~ Move to Windows PE Header Offset If Not FileSetPos($hFile, $iOffset, 0) Then ExitLoop $iExit = -2 ;~ Read in IMAGE_FILE_HEADER + Magic Number $bBuffer = FileRead($hFile, 26) If @error Then ExitLoop $iExit = 3 ; "PE/0/0" in hex (endian swapped) If BinaryMid($bBuffer, 1, 4) <> 0x00004550 Then ExitLoop ; Get NumberOfSections (need to use endian conversion) DllStructSetData($stEndian, 1, BinaryMid($bBuffer, 6 + 1, 2)) $nSections = DllStructGetData($stEndian, 1) ; Sanity check If $nSections * 40 > $nFileSize Then ExitLoop ;~ ConsoleWrite("# of Sections: " & $nSections & @CRLF) $bBuffer = BinaryMid($bBuffer, 24 + 1, 2) ; Magic Number check (0x10B = PE32, 0x107 = ROM image, 0x20B = PE32+ (x64) If $bBuffer = 0x10B Then ; Adjust offset to where "NumberOfRvaAndSizes" is on PE32 (offset from IMAGE_FILE_HEADER) $iOffset += 116 ElseIf $bBuffer = 0x20B Then ; Adjust offset to where "NumberOfRvaAndSizes" is on PE32+ (offset from IMAGE_FILE_HEADER) $iOffset += 132 Else $iExit = 4 SetError(Number($bBuffer)) ; Set the error (picked up below and set in @extended) to the unrecognized Number found ExitLoop EndIf ;~ 'Optional' Header Windows-Specific fields $iExit = -3 ;~ -> Move to "NumberOfRvaAndSizes" at the end of IMAGE_OPTIONAL_HEADER If Not FileSetPos($hFile, $iOffset, 0) Then ExitLoop $iExit = -2 ;~ Read in NumberOfRvaAndSizes $nDataDirectories = Number(FileRead($hFile, 4)) ; Sanity and error check If $nDataDirectories <= 0 Or $nDataDirectories > 16 Then ExitLoop ;~ ConsoleWrite("# of IMAGE_DATA_DIRECTORY's: " & $nDataDirectories & @CRLF) ;~ Read in IMAGE_DATA_DIRECTORY's (also moves file position to IMAGE_SECTION_HEADER) $bBuffer = FileRead($hFile, $nDataDirectories * 8) If @error Then ExitLoop ;~ IMAGE_DIRECTORY_ENTRY_SECURITY entry is special - it's "VirtualAddress" is actually a file offset If $nDataDirectories >= 5 Then DllStructSetData($stEndian, 1, BinaryMid($bBuffer, 4 * 8 + 1, 4)) $iCertificateAddress = DllStructGetData($stEndian, 1) DllStructSetData($stEndian, 1, BinaryMid($bBuffer, 4 * 8 + 4 + 1, 4)) $nCertificateSz = DllStructGetData($stEndian, 1) If $iCertificateAddress Then ConsoleWrite("Certificate Table address found, offset = " & $iCertificateAddress & ", size = " & $nCertificateSz & @CRLF) EndIf ; Read in ALL sections $bBuffer = FileRead($hFile, $nSections * 40) If @error Then ExitLoop ;~ DONE Reading File info.. ; Now to traverse the sections.. ; $iOffset Now refers to the location within the binary data $iOffset = 1 $nLastSectionOffset = 0 $nLastSectionSz = 0 For $i = 1 To $nSections ; Within IMAGE_SECTION_HEADER: RawDataPtr = offset 20, SizeOfRawData = offset 16 DllStructSetData($stEndian, 1, BinaryMid($bBuffer, $iOffset + 20, 4)) $nTemp = DllStructGetData($stEndian, 1) ;ConsoleWrite("RawDataPtr, iteration #"&$i&" = " & $nTemp & @CRLF) ; Is it further than last section offset? ; AND - check here for rare situation where section Offset may be outside Filesize bounds If $nTemp > $nLastSectionOffset And $nTemp < $nFileSize Then $nLastSectionOffset = $nTemp DllStructSetData($stEndian, 1, BinaryMid($bBuffer, $iOffset + 16, 4)) $nLastSectionSz = DllStructGetData($stEndian, 1) EndIf ; Next IMAGE_SECTION_HEADER $iOffset += 40 Next ;~ ConsoleWrite("$nLastSectionOffset = " & $nLastSectionOffset & ", $nLastSectionSz = " & $nLastSectionSz & @CRLF) $iSucces = 1 ; Everything was read in correctly Until 1 $iErr = @error FileClose($hFile) ; No Success? If Not $iSucces Then Return SetError($iExit, $iErr, $aRet) ;~ Now to calculate the last section offset and size to get the 'real' Executable end-of-file ; [0] = Overlay Start $aRet[0] = $nLastSectionOffset + $nLastSectionSz ; Less than FileSize means there's Overlay info If $aRet[0] And $aRet[0] < $nFileSize Then ; Certificate start after last section? It should If $iCertificateAddress >= $aRet[0] Then ; Get size of overlay IF Certificate doesn't start right after last section ; 'squeezed-in overlay' $aRet[1] = $iCertificateAddress - $aRet[0] Else ; No certificate, or < last section - overlay will be end of last section -> end of file $aRet[1] = $nFileSize - $aRet[0] EndIf ; Size of Overlay = 0 ? Reset overlay start to 0 If Not $aRet[1] Then $aRet[0] = 0 EndIf $aRet[2] = $iCertificateAddress $aRet[3] = $nCertificateSz $aRet[4] = $nFileSize Return $aRet EndFunc FilePEOverlayExtract.au3 ~prev downloads: 34 Updates: 2013-08-09-rev2: Fixed: Didn't detect 'sandwiched-in' Overlays - Overlays appearing between the end of code/data and before a Certificate section Changed: UDF now returns an array of information: Overlay offset and size, Certificate offset and size, and filesize Fixed: Overlays < 32 bytes may have been written incorrectly 2013-08-09: Fix: Certificate Table now identified and excluded from false detection as Overlay. 2013-08-07: Fix: Section Offsets that start beyond the filesize are now accounted for. I'm not sure when this happens, but it's been reported to happen on other sites. Modified: A more reasonable filesize limit. Modified: Option to Extract just the Executable without Overlay, or the Overlay itself 2013-08-03: Fixed: Calculation of FileRead data was off by 16 (which still worked okay, but was not coded correctly!) Fixed: @extended checking after calls to other code
- 21 replies
-
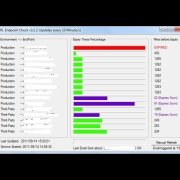
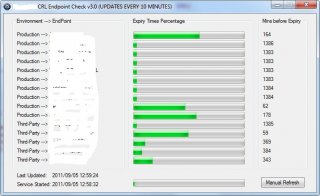
I've created this script to be able to download certificate revocation lists and check when they expire for multiple CRL's for work. The tool I have created seems to work but I'm worried It will have a memory leak or keep using more and more handles until the machine it is running on locks up. The tool uses a csv file that has the name of the CRL, the download location, a reference name for it and I'm now working on a notification bit that will email either the person responsible of an on-call email if the CRL expires. One of the problems I have is that I would normally create the labels and then update them within the while statement but I can't seem to be able to figure out how to referenece back to the array at the location I want the data to be updated. I tried creating the labels and progress bars but how do I reference each variable?? Here is the code minus a few bits: #include <Constants.au3> #include <Date.au3> #include <GUIConstantsEx.au3> #include <WindowsConstants.au3> #include <Array.au3> #include <File.au3> #include <INet.au3> Dim $aRecords, $Results, $Effective_date, $Expiry_Details, $Expiry_DetailsData, $CertUtilLogs, $FILE If Not _FileReadToArray("CRL_Check.csv", $aRecords) Then MsgBox(4096, "Error", " Error reading log to Array error:" & @error) Exit EndIf $mainWindow = GUICreate("CRL Endpoint Check v3.0 (UPDATES EVERY 10 MINUTES)", 700, (($aRecords[0] * 20) + 100)) Opt("TrayIconHide", 1) Opt("GUIOnEventMode", 0) ; Email Settings $s_SmtpServer = "*** REMOVED ***" $s_helo = "EHLO CRL_Endpoint_Check_v3.0" $s_first = -1 $s_FromName = "CRL Endpoint Check v3.0" $s_FromAddress = "*** REMOVED ***" Dim $as_Body[2] GUISetState() GUICtrlCreateGroup("Environment ---> EndPoint", 20, 10, 250, (($aRecords[0] * 20) + 40)) GUICtrlCreateGroup("Expiry Times Percentage", 280, 10, 280, (($aRecords[0] * 20) + 40)) GUICtrlCreateGroup("Mins before Expiry", 570, 10, 110, (($aRecords[0] * 20) + 40)) $LastUpdate = GUICtrlCreateLabel("Last Updated...", 30, (($aRecords[0] * 20) + 55), 200, 17) GUICtrlCreateLabel("Service Started: " & _NowCalc(), 30, (($aRecords[0] * 20) + 75), 200, 17) $RefreshProgress = GUICtrlCreateProgress(290, (($aRecords[0] * 20) + 70), 250, 17) $RefreshButton = GUICtrlCreateButton("Manual Refresh", 575, (($aRecords[0] * 20) + 65), 100, 25) GUICtrlSetData($RefreshButton, "Updating") GUICtrlSetState($RefreshButton, $GUI_DISABLE) $line = 40 While 1 For $x = 1 to $aRecords[0] $Endpoints = StringSplit($aRecords[$x], ",") $s_ToAddress = $Endpoints[4] If Not FileExists($Endpoints[1]) Then DirCreate($Endpoints[1]) EndIf $EndPointsLabel = GUICtrlCreateLabel($Endpoints[1] & " ---> " & $Endpoints[2], 30, $line, 220, 17) $MinsLeft = GUICtrlCreateLabel("** Updating **", 580, $line, 95, 17) $ProgressCreate = GUICtrlCreateProgress(290, $line, 250, 17) #Alternate Local $hDownload = InetGet($Endpoints[3], $Endpoints[1] & "\" & $Endpoints[2] & ".crl", 3, 1) Do Sleep(500) Until InetGetInfo($hDownload, 2) ; Check if the download is complete. Local $aData = InetGetInfo($hDownload) ; Get all information. InetClose($hDownload) ; Close the handle to release resourcs. If $aData[4] <> 0 then GUICtrlSetData($MinsLeft, "Download ERR") GUICtrlSetColor($MinsLeft, 0xff0000) ; Red GUICtrlSetData($ProgressCreate, "0") Sleep(500) $line = $line + 20 Else Sleep(500) $line = $line + 20 ;****************************************************************************** ;Interrogating the CRL with Certutil.exe and dumping to file $CertUtilLogs = FileOpen($Endpoints[1] & "\" & $Endpoints[2] & ".txt", 2) If $CertUtilLogs = -1 Then MsgBox(0, "Error", "Unable to create CRL Dump file. May be a file permission problem.") Exit EndIf local $Run = Run(@ComSpec & " /c " & "certutil.exe " & $Endpoints[1] & "\" & $Endpoints[2] & ".crl", "", @SW_HIDE, $STDOUT_CHILD) local $Certutilline Sleep(50) While 1 $Certutilline = StdoutRead($Run) If @error Then ExitLoop Sleep(200) FileWriteLine($CertUtilLogs, $Certutilline) Wend FileClose($CertUtilLogs) Sleep(50) ;****************************************************************************** ;****************************************************************************** ;Opening dumped file and processing to look for effective and expity date to calculate CRL duration $FILE = FileOpen($Endpoints[1] & "\" & $Endpoints[2] & ".txt", 0) If $FILE = -1 Then MsgBox(0, "Error", "Unable to open file so service probably isn't responding to commands.") Exit EndIf While 1 $READLINE = FileReadLine($FILE) If @error = -1 Then ExitLoop $Effective_date = StringRegExp($READLINE, ' ThisUpdate: (.*)', 2) For $I = 0 To UBound($Effective_date) - 1 $Effective_dateData = $Effective_date[1] Next $Expiry_Details = StringRegExp($READLINE, ' NextUpdate: (.*)', 2) For $I = 0 To UBound($Expiry_Details) - 1 $Expiry_DetailsData = $Expiry_Details[1] Next WEnd FileClose($FILE) ;****************************************************************************** ;****************************************************************************** ;Reformatting expiry details to suite date/time convention $date = StringSplit($Expiry_DetailsData, " ") ; Format the time If $date[3] = "PM" Then $hour = StringSplit($date[2], ":") If $hour[1] = 12 Then $hoursplit = 12 Else $hoursplit = $hour[1] + 12 If $hoursplit = 24 Then $hoursplit = 0 Else $hoursplit = $hour[1] + 12 EndIf EndIf EndIf If $date[3] = "AM" Then $hour = StringSplit($date[2], ":") $hoursplit = $hour[1] If $hoursplit = 12 Then $hoursplit = 0 Else $hoursplit = $hour[1] EndIf EndIf ;format the date $datesplit = StringSplit($date[1], "/") $FormattedDate = $datesplit[3] & "/" & $datesplit[2] & "/" & $datesplit[1] & " " & $hoursplit & ":" & $hour[2] & ":00" ;Date difference to _NowCalc() for minutes to expiry $iDateCalc = _DateDiff('n', _NowCalc(), $FormattedDate) ;****************************************************************************** ;****************************************************************************** ;Reformatting effective details to suite date/time convention $date1 = StringSplit($Effective_dateData, " ") ; Format the time If $date1[3] = "PM" Then $hour1 = StringSplit($date1[2], ":") If $hour1[1] = 12 Then $hoursplit1 = 12 Else $hoursplit1 = $hour1[1] + 12 If $hoursplit1 = 24 Then $hoursplit1 = 0 Else $hoursplit1 = $hour1[1] + 12 EndIf EndIf EndIf If $date1[3] = "AM" Then $hour1 = StringSplit($date1[2], ":") $hoursplit1 = $hour1[1] If $hoursplit1 = 12 Then $hoursplit1 = 0 Else $hoursplit1 = $hour1[1] EndIf EndIf ;format the date $datesplit1 = StringSplit($date1[1], "/") $FormattedDate1 = $datesplit1[3] & "/" & $datesplit1[2] & "/" & $datesplit1[1] & " " & $hoursplit1 & ":" & $hour1[2] & ":00" ;Date difference to _NowCalc() $iDateCalc1 = _DateDiff('n', $FormattedDate1, _NowCalc()) $iDateCalc2 = _DateDiff('n', $FormattedDate1, $FormattedDate) $ResultPercent = (($iDateCalc1 / $iDateCalc2) * 100) ;****************************************************************************** GUICtrlSetData($ProgressCreate, $ResultPercent) If $iDateCalc < "55" Then GUICtrlSetData($MinsLeft, $iDateCalc & " (Expires Soon)") GUICtrlSetColor($MinsLeft, 0xff0000) ; Red Else GUICtrlSetColor($MinsLeft, 0x000000) ; Black EndIf If $iDateCalc < 1 Then GUICtrlSetData($MinsLeft, "Expired") GUICtrlSetData($ProgressCreate, 100) $s_Subject = "CRL Endpoint Check v3.0 - CRL (" & $Endpoints[2] & ") has expired" $as_Body[0] = "CRL Endpoint Check v3.0 from " & @ComputerName & @CRLF $as_Body[1] = "Please contact the CRL privider and let them know their CRL has expired." & @CRLF & "CRL (" & $Endpoints[2] & ".crl) expired at: " & $FormattedDate & @CRLF & @CRLF & "Endpoint URL: " & $Endpoints[3] $Response = _INetSmtpMail ($s_SmtpServer, $s_FromName, $s_FromAddress, $s_ToAddress, $s_Subject, $as_Body, $s_helo, $s_first) Else GUICtrlSetData($MinsLeft, $iDateCalc) EndIf FileDelete($Endpoints[1] & "\" & $Endpoints[2] & ".txt") FileDelete($Endpoints[1] & "\" & $Endpoints[2] & ".crl") EndIf Next GUICtrlSetData($LastUpdate, "Last Updated: " & _NowCalc()) $line = 40 ;****************************************************************************** GUICtrlSetData($RefreshButton, "Manual Refresh") GUICtrlSetState($RefreshButton, $GUI_ENABLE) GUICtrlSetData($RefreshProgress, 0) $Timer = TimerInit() $ProgressStep = "" $TimerValue = 600000; 10 minute approx While 1 $msg = GUIGetMsg() Select Case $msg = $RefreshButton GUICtrlSetData($RefreshButton, "Updating") GUICtrlSetState($RefreshButton, $GUI_DISABLE) GUICtrlSetData($RefreshProgress, 0) $Timer = TimerInit() ExitLoop Case $msg = $GUI_EVENT_CLOSE; Or $msg = $BUTTON2 GUIDelete() FileClose($FILE) FileClose($CertUtilLogs) Exit EndSelect GUICtrlSetData($RefreshProgress, (TimerDiff($Timer) / $TimerValue * 100)) If TimerDiff($Timer) > $TimerValue Then GUICtrlSetData($RefreshProgress, 100) $Timer = TimerInit() GUICtrlSetData($RefreshButton, "Updating") GUICtrlSetState($RefreshButton, $GUI_DISABLE) ExitLoop EndIf WEnd WEnd The input file looks like this Production,testcrl1,http://testsite1/latest.crl,testcrl1_latest.crl,test1@website.com Production,testcrl2,http://testsite2/latest.crl,testcrl2_latest.crl,test2@website.com The first tab is the environment. the second is a lable for the CRL, the third is the CRL download address and the last is the email address to email to. Attached is a screenshot of what it looks like after the initial CRL processing then waiting. If someone has a better way (as I'm sure there is) of doing this then please let me know. I have commented some of it but not all so sorry if it becomes confusing. Cheers Justin